Image Source: https://www.agitraining.com/design-news/adobe-training-news/major-security-vulnerability-identified-adobe-flash
In November, our security analysts uncovered a phishing method taking advantage of a vulnerability in Office 365 to bypass all of Microsoft's security. The vulnerability left all Office 365 users vulnerable, regardless of if they were using ATP or not. We saw this method of attack attempted on over 90% of Avanan's Office 365 customers.The vulnerability was discovered when we noticed a large number of hackers using zero-width spaces (ZWSPs) to obfuscate links in phishing emails to Office 365, hiding the phishing URL from Office 365 Security and Office 365 ATP. This method bypassed both Office 365's URL reputation check and Safe Links URL protection that is part of ATP.
The attacks we observed taking advantage of the Z-WASP vulnerability were very simple in structure, but their potential impact (had we not blocked them) would have been extremely devastating.
To demonstrate this vulnerability, we performed a test, which you can watch in the video below. First, we sent a malicious URL to an Office 365 inbox without any ZWSP characters inserted in the URL. Then, we sent the same malicious URL again with ZWSP characters inserted into the URL.
What are Zero-Width Spaces (ZWSPs)?
ZWSPs can be thought of as "empty space" characters, or characters that render to spaces of zero-width. There are 5 ZWSP entities:- ​ (Zero-Width Space)
- ‌ (Zero-Width Non-Joiner)
- ‍ (Zero-Width Joiner)
-  (Zero-Width No-Break Space)
- 0 (Full-Width Digit Zero)
As detrimental as ZWSPs are in the context of this vulnerability, they actually take part in formatting the internet we see everyday. Some common uses for ZWSPs include:
- Fingerprinting articles and documents
- Formatting foreign languages
- Breaking long words at the end of a line and continuing them on the next line
How Z-WASP Phishing Attacks Work
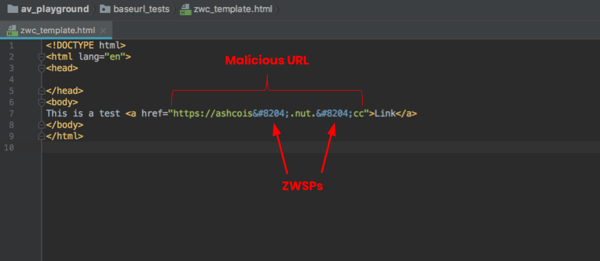
In a Z-WASP phishing attack, the Zero-Width Non-Joiner (‌) is added to the middle of a malicious URL within the RAW HTML of an email.
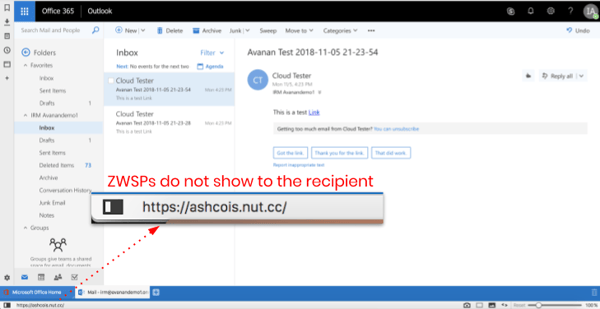
Hover over the URL below to see the difference between how Microsoft Security viewed the URL containing ZWSPs, and how the URL was presented to the recipient.
Z-WASP Signals an Evolution in Office 365 Phishing Attacks
The Z-WASP attack is another chain in a list of exploits that are designed to obfuscate malicious content and confuse Office 365 security. Two similar exploits Avanan uncovered last year include the baseStriker and ZeroFont attacks .In the baseStriker attack, the URL was split into two parts: the base and href tags. Microsoft only scanned the base tag, allowing the malicious part through.
The ZeroFont attack used text obfuscation vulnerabilities to bypass ATP by adding characters with font-size 0 to trick the natural language analysis of Office 365 while the user was presented with the text of the phishing email.
The Z-WASP attack gestures to these two predecessors, but ultimately surpassed them in its ingenuity and simplicity.
How Avanan Caught the Attack
Avanan's machine learning anti-phishing scans emails after Office 365 Security (EOP and ATP), but before they reach the end-user’s inbox. Designed specifically to add security to the default layers provided by Microsoft Office 365 and google’s Gmail, the machine-learning algorithm will flag text obfuscation methods in addition to over 300 indicators in every email to the the emails flagged as malicious and blocked.Note: We reported the vulnerability to Microsoft on November 10th when we confirmed its nature. We worked with them continuously on assessing the scope of the vulnerability and as of January 9th the vulnerability has been remediated.
Source: Avana.com Downloaded: 20190113







0 Comments